FUD This, Bill!
Matrix Event Advisory – Slammer Worm Attack status 23:37Z 25JAN03: Ongoing; see Internet Storm Center event analysis
Because M$ SQL Server 2000 needs to be tucked in (“turn off Microsoft SQL servers until all current patches are applied; block ports UDP 1433 and 1434”), otherwise it’s a train wreck waiting for someone to act nasty, global web reachability dived below 75% around midnight EST.
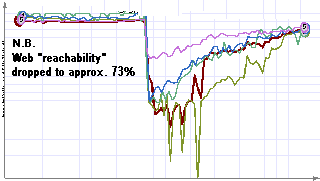
click for 1800Z 25JAN03 fullsize [thanks to MatrixNetSystems for their fine work])
Matrix NetSystem reports “ISS MSS (Managed Security Services) has recorded 2.5 million attacks from 12 a.m. to 3 a.m. EST (GMT-5) on January 25, 2003.” The Internet Storm Center graph shows a peak of “7985 packets / sources / targets per minute”:
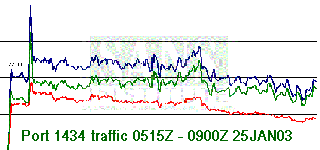
click for fullsize [thanks to ISC for their fine work])
… at its peak, packet loss touched 16%. Viz.:
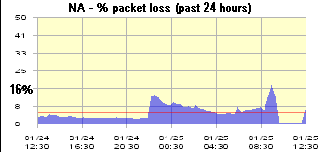
At one point I saw latency on UUDP reach “BIG” (if 1500 mSec is “critical”, then what latency is characterised as “BIG”?!) Viz.:
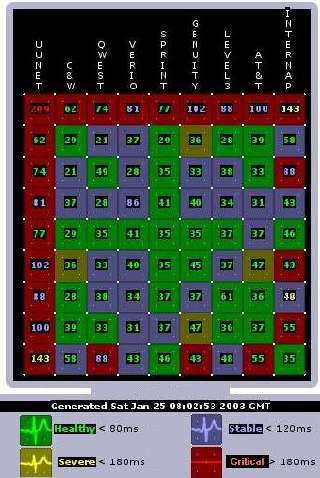
ISC’s “port report” (which also carries some revealing data graphs) describes two different 1434 attacks:
CAN-2002-0650 – The keep-alive mechanism for Microsoft SQL Server 2000 allows remote attackers to cause a denial of service (bandwidth consumption) via a “ping” style packet to the Resolution Service (UDP port 1434) with a spoofed IP address of another SQL Server system, which causes the two servers to exchange packets in an infinite loop. [“Single ms-sql servers have been reported to generate traffic in excess
of 50 MBit/sec. after being infected.” h_b]CAN-2002-0649 – Multiple buffer overflows in SQL Server 2000 Resolution Service allow remote attackers to cause a denial of service or execute arbitrary code via UDP packets to port 1434 in which (1) a 0x04 byte causes the SQL Monitor thread to generate a long registry key name, or (2) a 0x08 byte with a long string causes heap corruption.
Sources:
Primary: ISC Incident Analysis … the must read. (RTFA?)
Others: MSSQL-UDP Advisory from NGSSoftware Insight Security Research ([M$’s] “SQL Server 2000 exhibits two buffer overrun vulnerabilities that can be exploited by a remote attacker without ever having to authenticate to the server. What further exacerbates these issues is that the attack is channeled over UDP.”); Internet Health Report (n.b.: UUNET is still reporting some critical latency as I blog this); Matrix NetSystems: Internet Average; Internet Security Center: Current Internet Threat Level (it was Crit4 this afternoon); Network Overview | Internet Traffic Report (showed Asia getting thrashed); The Digital Offense with some worm source and notes
For discussion, I’d suggest two /. threads: the one from 7AM Saturday (“Since about midnight EST almost every host on the internet has been receiving a 376 byte UDP payload on port ms-sql-m (1434) from a random infected server. “) and a second one I found just now: DDoS for Fun and Profit (“First there’s the Microsoft worm, reported earlier [above], which in addition to all the other damage has apparently knocked Microsoft’s Windows XP activation servers [see my rant, below, which includes an exceprt from M$ ”Maintenance”] (and Bank of America ATMs) off the net. Then we’ve got a report about the ongoing demise of DALnet … And Canada discovers a risk to online voting.” Note: I happened to be listening to the New Democratic Party’s leadership convention live: yes, they did use Web voting; and yes, they did encounter problems consistent with this worm [were they using M$ $erver $000?. Happily, things worked out very well.])
<rant>Now, what kind of bottom-feeding Enron type says, “Oh, well, we don’t call it a bug” and then goes on his merry way, pulling down management salary as a software engineer. You think I’m blowing smoke? Dig this, “M$ Maintenance”, from hardocp.com :
“It’s 2:20 CST and I’m trying to activate a copy of XP. I need to, because this repair/upgrade (changed mb, disk controller, video, hdisk, NIC, RAM, USB revision, CPU, etc) I can’t logon without activation.
Except, I CAN’T ACTIVATE. I am told there is no way ANY copy of XP can be activated in the next 5 hours because of (drum roll)
** Routine maintenance **. I mean, I asked: I said
“You don’t have some little stand-alone machine that reads a DVD database so you could stand in line and do it?â€
“You don’t have a couple hundred “last resort†number ranges? You can call me back tomorrow!!!â€
“There’s not some guy you can go ask? Ya can’t call Bill at home?â€
So, I gotta stop my project for some unknown length of time. Good thing I’m not updating a medical drug interaction database, or an available transplant database, or a process flow control system or a hazardous atmosphere measurement system or a BUNCH of other possibilities. In my case, either I miss the superbowl, or my car dealer can’t find and order Volvo cars on Monday. Life will continue.
But, I’m still seriously pissed. Call ‘em at 888-571-2048 and try for activation.
And let’s think about the true meaning of the fact you can’t release liability for the consequential damage resulting from negligence. I mean, I have NEVER heard about “routine maintenance†on the 24.7.365 activation promise…
Well, on to the next job…“
When the credibility balance between commercial and open source products became a thread in evolt’s [thelist], David Kaufman put together an assessment that included this block:
“CNN spared MS the embarassment of pointing out that this security flaw in
one of Microsoft’s flagship products, finally noticed and patched last summer (july of 2002) had previously existed in the SQL Server 2000 code for 2 and a half years, completely undetected and, according to the relevant MS security bulletin, the same bug also has also existed and reamined undetected in MSDE 2000, the “MS Data Engine” which shipped originally in October of 1998 (as part of Access 2000, per MS press release) and has now been on the market as production code for over three years.
In addition to SQL Server 2000 (Developer, Standard, and Enterprise Editions), the bug also affects just a couple of other MS tools, as well, according to[ this Internet Storm Center report].
[ … ]
yet amazingly, each of the well-paid teams of Microsoft developers responsible for reviewing the code for all of these core MS products have underwhelmed us once again by failing to review the un-sexier code bits to unearth this internet-stopping buffer overflow vulnerability, for years, allowing hackers to exploit it in yet another astonishingly newsworthy DDOS attack brought to you by Microsoft bugs.
ah well. no one’s perfect. not even a staff and a salary can replace simply giving a shit, now can it? i guess i’d just prefer my buffer overflows to be pointed out to me by self-styled volunteer security pundits causally perusing my open source code [ … ] “
Any wonder why kidz are bummed at their future prospects? You want your son or daughter caught in a 9/11 type attack? How about the image of him or her being hammered in the chest by a rocket-propelled grenade as s/he scrambles for cover behind some gawd-forsaken rock in some gawd forsaken desert fighting for some gawd-forsaken corporate power struggle? Get righteous!!
Like democracy itself, the ‘net is vulnerable to short-sightedly self-indulgent ineptitude. You can quote me on that.</rant>